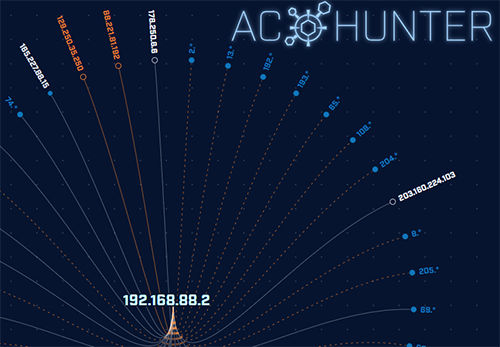
AC-Hunter™ is a software solution that continuously threat hunts your network to identify which of your systems have been compromised.
There is no need to install agents on endpoints – AC-Hunter monitors and verifies all network devices, including IoT, IIoT, and BYOD, regardless of operating system or hardware.
The simple-to-use interface is focused on enabling threat hunting success for everyone, from junior analysts to seasoned professionals.